Spinal Hack

Spinal Hack
by Ed Skoudis, November 2003
After a brief resurgence in Japan, Spinal Tap's popularity plummeted again. The rock and roll group, widely recognized as England's loudest band, was back to doing opening acts for a traveling puppet theater.
To get out of this death spiral, David St. Hubbins and Nigel Tufnel, the band's leaders, used their chameleon-like powers of adaptation to move into new musical territory. Instead of hard-hitting rock music full of sophomoric sexual innuendo, the radically transformed band would now perform hard-hitting techno music full of sophomoric sexual innuendo. They rewrote some of their classic tunes to be more techno friendly, including "Big BIOS", "Tonight I'm Gonna Hack You Tonight", and "Gimme Some Root Sploits," all of which would be released on their new album, Sniff the Network.
To help win fans over to their new sound, the band set up a web site to serve up sample MP3s of their latest jams on the Internet. Although David and Nigel were closer than brothers, they didn't see eye to eye on a choice of operating systems for the web site. Nigel was a hard-core Linux geek, while David was a Windows aficionado. After a renewed cycle of bickering, groupies, band break-ups, groupies, temporary reunions, and more groupies, the band settled on Windows 2000.
Tragically, within weeks, the web site system administrator hired by the band met with an untimely death, spontaneously combusting in a rare cubicle accident. Short on funds for hiring another web administrator, the band selected Nigel to run the web site, given his supposed in-depth technical knowledge (at least when compared with the rest of the band.)
After taking over the web site, Nigel noticed that some intruder had replaced their breathtaking new music with songs performed by their nemesis, Duke Fame. Spinal Tap's website had been defaced with no-talent wanker music! Nigel rapidly deleted Duke's files, restoring Tap's own content. But, after a couple of minutes, the lame music reappeared. The attacker must have put a backdoor on the system.
To investigate, Nigel logged in as an Administrator and invoked the Windows Task Manager by hitting CTRL+ALT+DEL and selecting "Task Manager". After clicking on the "Processes" tab and sorting it by "Image Name", Nigel saw the following window:
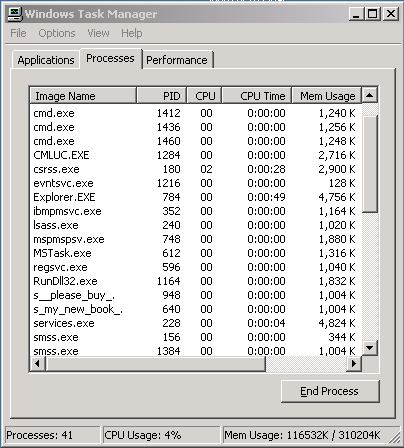
Although he was a Linux guy, Nigel thought that one of the running Windows processes seemed unusual; it appeared to be out of place. He selected the strange process and hit the "End Process" button. Unfortunately, Windows presented Nigel with this error message:
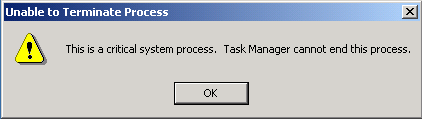
Nigel looked at the dialogue box quizzically, and exclaimed, "I get the sense of it... I just don't understand it!"
Help Nigel make sense of his dilemma by answring the following four questions. The best answers will win a prize:
•1) Which process was most ususual and therefore most likely to be the backdoor planted on the machine?
•2) How could Nigel determine whether this process was listening on a TCP or UDP port, the user name it was running under, and the file that was executed to invoke the process? Please list any built-in or third-party tools you would use to answer this question.
•3) Why couldn't Nigel kill this process using the "End Process" button in the Windows Task Manager?
•4) How could Nigel actually kill the attacker's process without rebooting the box?
Here are my answers, as well as the winners of this challenge!
